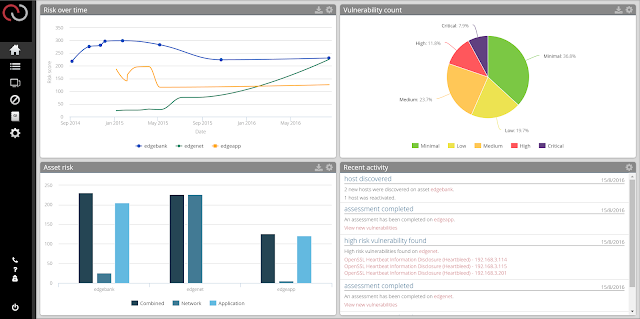
Convergence of data, economies, supply chains & critical infrastructure and it all needs to be secure...welcome to the Internet. As a practitioner in the software development and security industries for over 15 years, I've got to say it has never felt like a job. For people to like their jobs it's a blessing, particularly as my skillset is in demand. Demand is based on need and given the proliferation of internet technologies for literally anything (finance, military, energy, mobile, IoT) is does not see to be getting any less busy. As with anything if there is a demand for something there comes a tipping point. Be it energy, clean water, food security or even Internet security. As a result there are some knock-on effects and many are the result of a capacity to deliver . Given so many different industry verticals are all converging into a single approach to delivery (the Internet) the responsibility of securing such a global machine is only getting more de